PassCypher HSM PGP: how to manage your passwords with a browser extension
PassCypher HSM PGP is a free and anonymous password manager with anti-phishing and corrupted password control. It allows you to generate, manage and use labels containing login IDs, passwords and original urls, passphrases, AES 256 PGP encryption keys and more, such as your various SSH keys, with a browser extension. It works on Chromium-based or Firefox-based web browsers. It is distributed by www.fullsecure.link. In this tutorial, you will learn how to:
- create, manage and use encrypted labels in AES-256 PGP with entropy control based on Shannon
- activate the counter-attack by BITB and manually check for corrupted passwords
- select the language of PassCypher different from the browser language
- enable automatic login or auto fill
- use the PassCypher Engine software with PassCypher HSM PGP for automatic encryption and decryption with a segmented key pair with 2FASelon la définition de Wikipédia 2FA, est l'anagramme de (Two-factor authentication en anglais). Il s'agit de... More function
- generate and create encrypted SSH keys with or without a password with entropy control based on Shannon
- set up and use the PassCypher NFCNear Field Communication (NFC) : il s'agit d'une technologie de connectivité sans fil à courte... More HSM product for Android NFCNear Field Communication (NFC) : il s'agit d'une technologie de connectivité sans fil à courte... More phones
You will also learn about some of the benefits and examples of use with PassCypher HSM PGP.
Enhancing Data Security with PassCypher HSM PGP’s Segmented Keys
Mitigating Cyber Threats through Decentralization and Encryption
PassCypher HSM PGP’s approach to data security fundamentally transforms traditional methods. By eliminating the need for a server or database and encrypting each label individually with AES-256, PassCypher HSM PGP erects a formidable barrier against a variety of cyber threats. Below, we explore the specific attacks rendered impossible by this innovative security model:
Server-Based Attacks
Without a server, there is no central point for attackers to target, rendering server-based attacks like DDoS (Distributed Denial of Service) or server hacking irrelevant. This decentralization ensures that even if one part of the system is compromised, the integrity of the whole remains intact.
Database Exploits
The absence of a database eliminates risks associated with SQL injection, data theft, or unauthorized access to stored information. Data is processed in real-time and never stored, leaving no opportunity for attackers to exploit historical data.
Data Interception
As all labels are encrypted individually, intercepting data in transit becomes futile. Attackers cannot decrypt the information without the corresponding keys, ensuring that data remains confidential and secure.
Replay Attacks
The use of segmented keys for 2FASelon la définition de Wikipédia 2FA, est l'anagramme de (Two-factor authentication en anglais). Il s'agit de... More prevents replay attacks, where an attacker could use previously captured data. Each authentication is unique and time-sensitive, making it impossible to use old data for unauthorized access.
Phishing
Phishing attacks that rely on deceiving users to gain access to server-stored credentials are ineffective. Since data is not centrally stored, there are no credentials to steal from a server.
Insider Threats
The risk of insider threats is reduced as there is no centralized repository of data for malicious insiders to exploit. Users have full control over their data, and only they can access it with their segmented key pair or AES PGP key and password security.
Serverless Data Handling
PassCypher products function entirely in volatile memory, ensuring real-time processing without reliance on servers or databases. This attribute enhances the system’s resilience against cyber attacks.
Full Data Control
Users maintain absolute control over their data, which remains unstored and unsynced with any cloud service. This autonomy safeguards users’ privacy and security.
Enhanced Privacy
The absence of third-party storage negates risks associated with hacking, data breaches, or data loss. Users’ data stays private and secure.
Exclusive Access
Only the user, equipped with their unique segmented key pair or AES PGP key and password, can access their data. This exclusive access strengthens the security of users’ information.
By leveraging segmented keys and individual AES-256 encryption, PassCypher HSM PGP ensures a robust security framework that effectively counters a broad spectrum of potential cyber threats. This model not only bolsters security but also grants users complete control over their data privacy.
How to create segmented key pairs with PassCypher HSM PGP browser extension
PassCypher HSM PGP is a browser extension that lets you encrypt and decrypt your data with AES-256 PGP. It works on Chromium-based or Firefox-based web browsers. It is distributed by www.fullsecure.link. To use this extension, you need to have a PassCypher Engine license, which allows you to automate the encryption and decryption process with segmented keys. In this article, you will learn:
- What are segmented keys and why they are secure
- How to generate a segmented key pair with PassCypher HSM PGP
- How to use the segmented key pair for encryption and decryption
- What are some examples of using segmented keys for different scenarios
- How PassCypher products work without a server or a database

What are segmented keys and why they are secure
Segmented keys are a type of encryption keys that are split into two parts. One part is stored in the browser’s local storage and the other part is stored in a storage device of your choice, such as a contactless secure USB with Evikey NFCNear Field Communication (NFC) : il s'agit d'une technologie de connectivité sans fil à courte... More HSM technology. To decrypt the data, you need both parts of the key.
Segmented keys provide enhanced security because they require two keys to decrypt the data. If one key is compromised, the other key is still needed to decrypt the data. Moreover, segmented keys allow you to customize the security level according to your needs. For example, you can choose to store the second key on a secure hardware device, such as an Evikey NFCNear Field Communication (NFC) : il s'agit d'une technologie de connectivité sans fil à courte... More HSM USB.
How to generate a segmented key pair with PassCypher HSM PGP
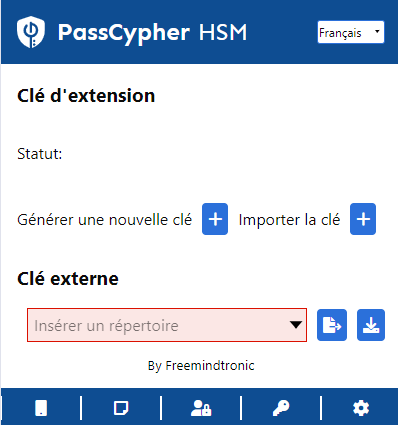
To generate a segmented key pair with PassCypher HSM PGP, you need to click on the PassCypher icon in your web browser. This will open a window where you can choose to generate a new key or import an existing one. You can also choose to add a password to your key for extra security.
The image below shows the window that pops up when you click on the PassCypher icon in a Chromium or Firefox-based web browser. This window is only useful if you have purchased a PassCypher Engine license, which allows you to fully automate PassCypher HSM PGP encryption in AES-256 with segmented keys and instant connection from any storage device.
How to use the segmented key pair for encryption and decryption
Activating Segmented Keys for Encryption and Decryption: Initially, ensure both key parts are accessible. The browser’s local storage holds one, while a device like Evikey NFCNear Field Communication (NFC) : il s'agit d'une technologie de connectivité sans fil à courte... More HSM USB secures the other.
Encrypting Your Data: Next, create a label via the PassCypher icon in your browser. Select the label type, then encrypt it using the segmented keys and AES-256 PGP, guided by Shannon’s entropy.
Decrypting Your Data: Then, locate the label for decryption. Choose it from the list after clicking the PassCypher icon. Decrypt using the segmented keys with AES-256 PGP, again considering Shannon’s entropy.
Simplifying Login with Auto Features: Finally, utilize auto login or auto fill to streamline your website access. These features automatically input your credentials for sites with encrypted labels, offering an option for automatic login without manual clicks.
Versatile Applications of Segmented Keys
Segmented Keys: Diverse Uses Across Scenarios
Segmented keys adapt to various needs, offering tailored security solutions. Here are concise examples of their versatile applications for:
- Businesses: Segmented keys limit data access within company premises. For instance, a business might use an Evikey NFCNear Field Communication (NFC) : il s'agit d'une technologie de connectivité sans fil à courte... More HSM USB, locked via PassCypher NFCNear Field Communication (NFC) : il s'agit d'une technologie de connectivité sans fil à courte... More HSM with geofencing, to ensure employees access sensitive data only on-site.
- Individuals: People protect their credentials, like login IDs or encryption keys, using segmented keys. A user might keep the second key on an Evikey NFCNear Field Communication (NFC) : il s'agit d'une technologie de connectivité sans fil à courte... More HSM USB at home, securing personal data access to themselves.
- Portable Security: Users might encrypt the second key on a Bitlocker-secured USB, SD, or SSD, allowing data access from any Bitlocker-compatible computer.
- Cloud Access: Storing the second key encrypted in the cloud or NAS, accessible via VPN, enables data access from any VPN-supported device, with PassCypher ensuring decryption occurs in volatile memory only.
Segmented keys’ flexibility makes it challenging for attackers to predict the second key’s location, enhancing security.
How to generate your custom password with PassCypher HSM PGP browser extension
PassCypher HSM PGP is a browser extension that lets you encrypt and decrypt your data with AES-256 PGP. It works on Chromium-based or Firefox-based web browsers. It is distributed by www.fullsecure.link. To use this extension, you need to have a PassCypher Engine license, which allows you to automate the encryption and decryption process with segmented keys. In this article, you will learn how to generate your custom password with PassCypher HSM PGP.
What are encrypted labels?
Encrypted labels are data items that contain login IDs, passwords, original urls, passphrases, or AES 256 PGP encryption keys. You can create and use them with PassCypher HSM PGP browser extension. They are encrypted in AES-256 PGP with entropy control based on Shannon. This means that they are secure and hard to crack.
To create an encrypted label, you need to click on the PassCypher icon in your web browser. Then, you can choose the type of label you want to create. For example, you can create a label for a website login, a passphrase, a segmented password, or an AES 256 PGP encryption key. You can also choose to add a password to your label for extra security.
To use an encrypted label, you need to click on the PassCypher icon in your web browser. Then, you can search for the label you want to use. For example, you can use a label to log in to a website, to decrypt a file, or to access a service. You can also use the auto login or auto fill feature to make it easier.
How to generate your custom password
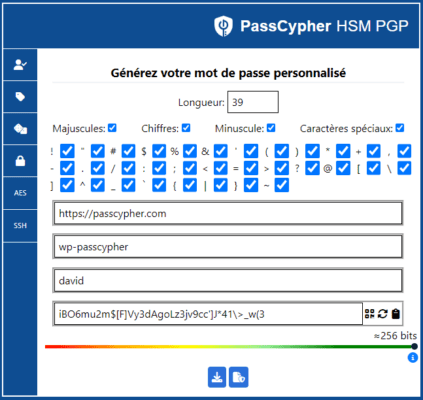
To generate your custom password, follow these steps:
- Set the length of your password. In this example, it is set to 39 characters, which corresponds to 256 bits of entropy.
- Select the types of characters that you want to include in your password (uppercase letters, numbers, lowercase letters, special characters) by checking the appropriate boxes.
- Enter the original URL, the identifier, and the password in the fields provided.
- Use the QR code icon to generate a QR Code coded compatible with PassCypher NFCNear Field Communication (NFC) : il s'agit d'une technologie de connectivité sans fil à courte... More HSM. This allows you to transfer your label to a contactless secure NFCNear Field Communication (NFC) : il s'agit d'une technologie de connectivité sans fil à courte... More HSM technology.
- The icon with two circular arrows is used to generate a random password according to the desired length. You can click on it until you get a password that you like.
- The clipboard icon allows you to copy the generated password. You can paste it in another application or document if you want.
- The color bar indicates the entropy level of the password based on the mathematical calculation of Shannon. The higher the entropy, the more secure the password is.
- You can download the label in JSON format unencrypted by using the button with a downward arrow. This allows you to save your label on your computer or another device.
- The button with a file and a shield allows you to indicate the AES-PGP key with or without a password that will be used to encrypt this label. This allows you to secure your label with AES-256 PGP encryption.
The image below shows the interface of PassCypher HSM PGP password generator. You can access it by clicking on the PassCypher icon in your web browser.

You have now generated your custom password with PassCypher HSM PGP. You can use it to log in to a website or a service securely and conveniently. You can also use the auto login or auto fill feature to make your login process easier and faster.
Here you will learn how and why to create a memorable passphrase with PassCypher HSM PGP
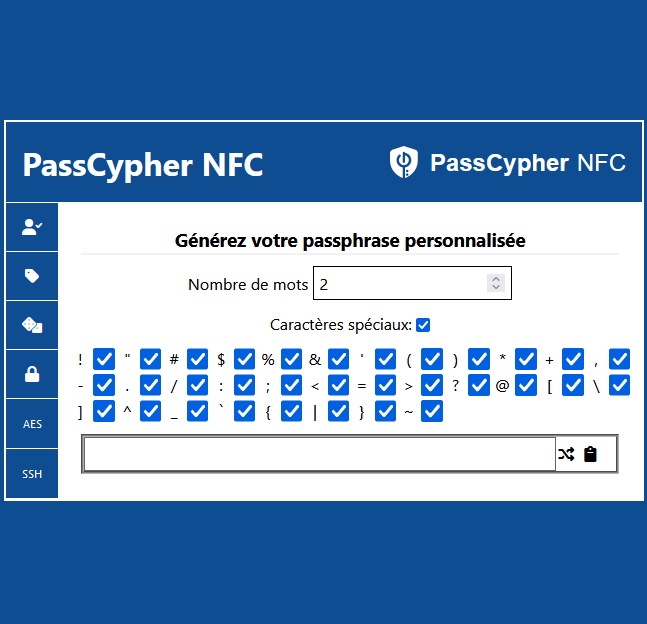
A passphrase is a sequence of words that you can use as a password. It is easier to remember than a random string of characters, but still secure if it has enough entropy. Entropy is a measure of how unpredictable a password is. The more entropy, the harder it is to guess or crack.
To create a passphrase with PassCypher HSM PGP, you need to click on the icon with two crossed arrows on the right side of the field where the passphrase is generated. You can click as many times as you want until you find a passphrase that you can easily remember.
The image below shows the interface of PassCypher HSM PGP passphrase generator. You can access it by clicking on the PassCypher icon in your web browser.